All Tags
AWS
ai
algorithm-design
architecture
browser
cloud
cloud-efficiency
cloud-principles
cost-reduction
data-centric
data-compression
data-processing
deployment
design
documentation
edge-computing
email-sharing
energy-efficiency
energy-footprint
enterprise-optimization
green-ai
hardware
libraries
llm
locality
machine-learning
maintainability
management
measured
microservices
migration
mobile
model-optimization
model-training
multi-objective
network-traffic
parameter-tuning
performance
queries
rebuilding
scaling
services
storage-optimization
strategies
tabs
template
testing
workloads
Tactic: One-sided infrastructure control
Tactic sort:
Dark Tactic
Type: Unsustainable Pattern
Category: edge-computing
Tags:
Title
One-sided infrastructure control
Description
If the owner of the edge infrastructure has malicious intentions, it is easy for him to cut access to the technology or control the people using it (e.g., in a dictatorship). This represents a social sustainability threat to anyone using the technology while not in full control of the equipment and applications in the infrastructure. In fact, security and privacy issues are mentioned as more prominent in edge than in cloud.
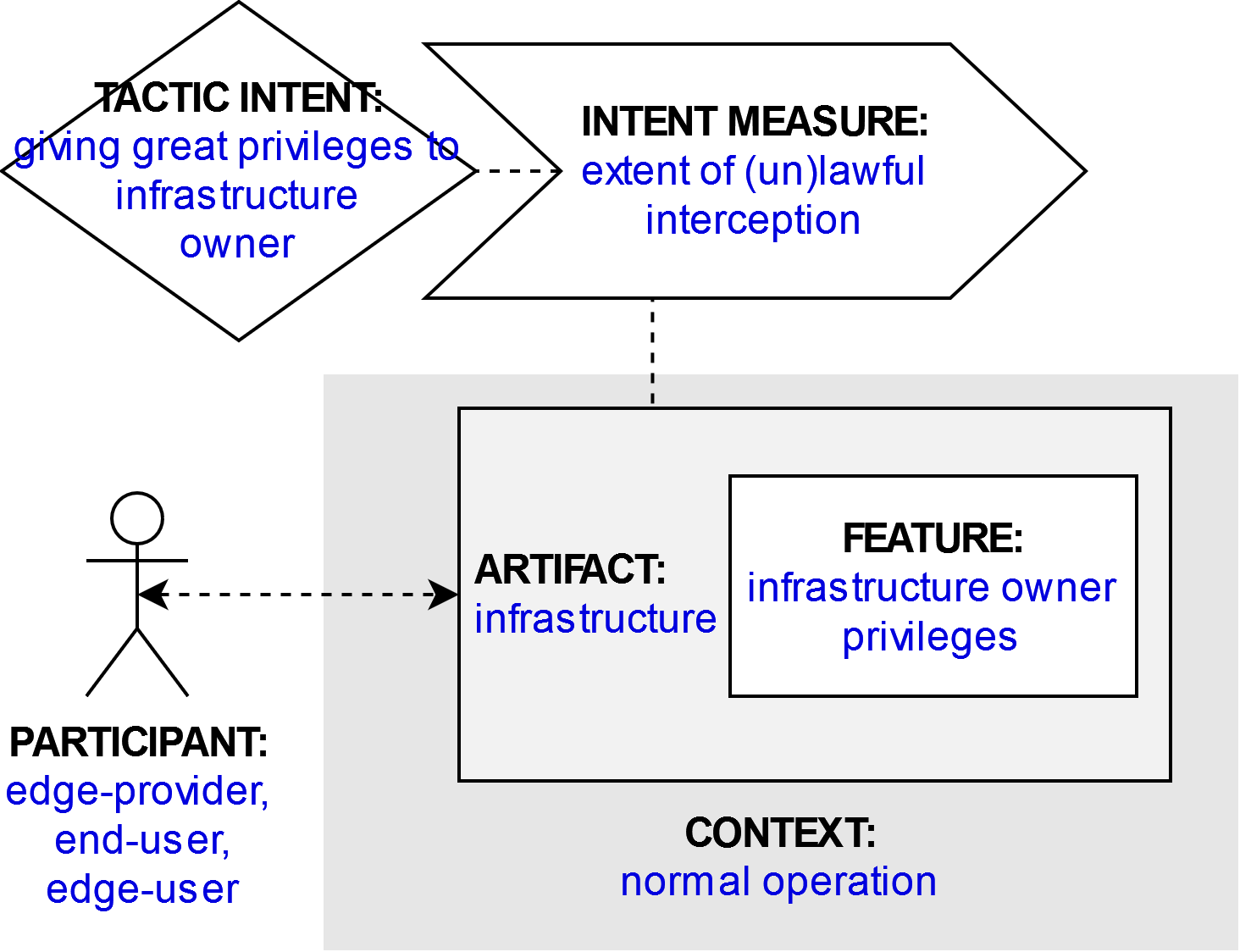
Participant
edge-provider, end-user, edge-user
Related artifact
Infrastructure
Context
Normal operation
Feature
Infrastructure owner privileges
Tactic intent
Giving great privileges to whoever owns the infrastructure
Intent measure
Extent of (un)lawful interception
Countermeasure
It is necessary to establish trust between the devices, for which there exist an important body of work (see the paper for references). Of course these trust evaluation mechanisms come with an overhead, as discussed in tactic 'trust overhead'.
Source
*The Dark Side of Cloud and Edge Computing* by Klervie Toczé, Maël Madon, Muriel Garcia and Patricia Lago (DOI: https://doi.org/10.21428/bf6fb269.9422c084)Graphical representation