All Tags
AWS
ai
algorithm-design
architecture
browser
cloud
cloud-efficiency
cloud-principles
cost-reduction
data-centric
data-compression
data-processing
deployment
design
documentation
edge-computing
email-sharing
energy-efficiency
energy-footprint
enterprise-optimization
green-ai
hardware
libraries
llm
locality
machine-learning
maintainability
management
measured
microservices
migration
mobile
model-optimization
model-training
multi-objective
network-traffic
parameter-tuning
performance
queries
rebuilding
scaling
services
storage-optimization
strategies
tabs
template
testing
workloads
Tactic: Unauthorized surveillance
Tactic sort:
Dark Tactic
Type: Unsustainable Pattern
Category: edge-computing
Tags:
Title
Unauthorized surveillance
Description
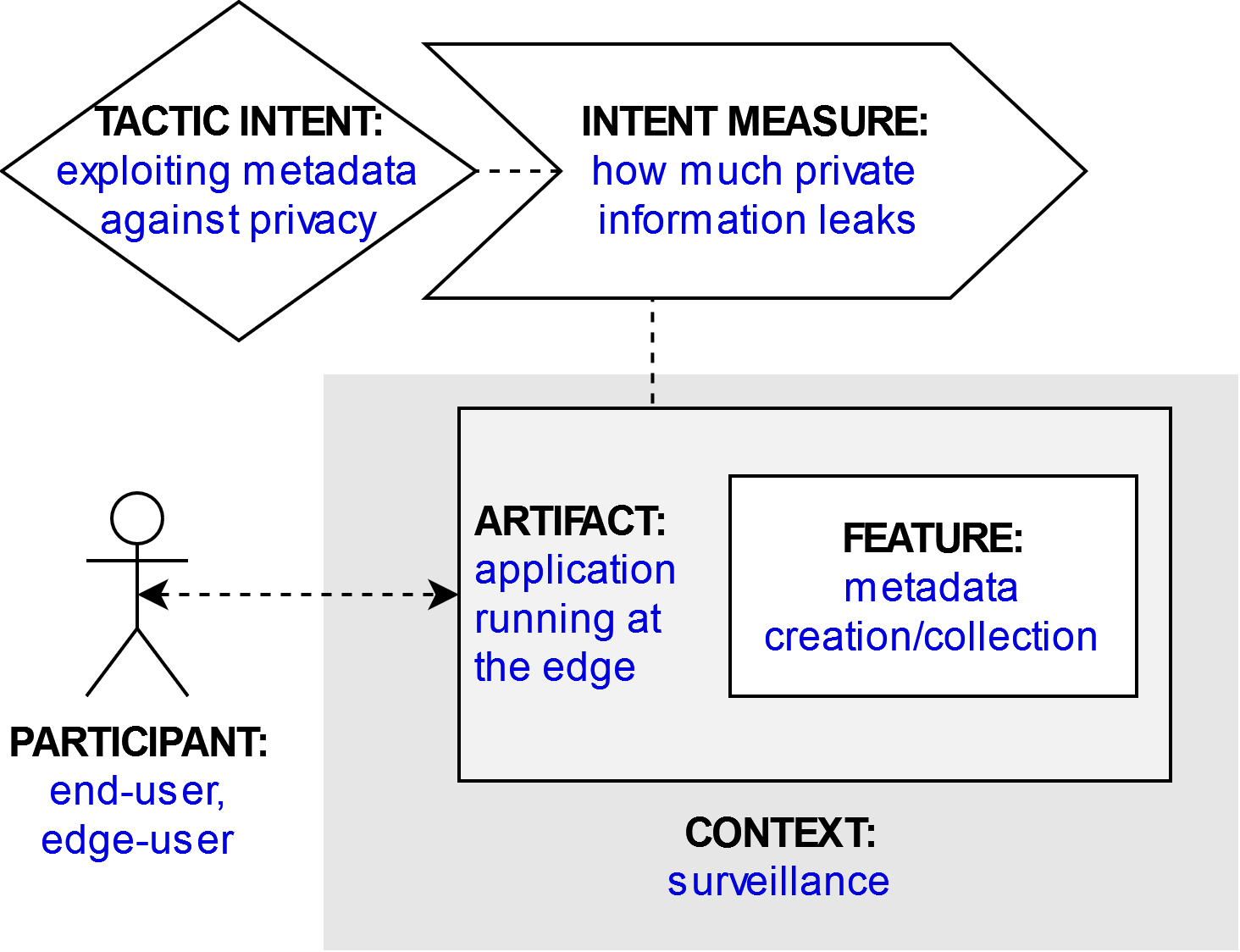
Because the edge is closer to the edge users and end users, access to applications running at the edge generate more and richer metadata, like the user geolocation (and movements) by monitoring the location of the edge device, or the presence and use of collocated applications e.g., for smart-home or IoT appliances. This enables exploiting metadata against privacy, sometimes authorized (e.g., in smart surveillance for safety reasons), but often unauthorized with malicious intents (e.g., facial spoofing, people tracking) or for commercial reasons (e.g., monitoring of customers behavior).
Participant
end-user, edge-user
Related artifact
Application running at the edge
Context
Surveillance
Feature
Metadata creation/collection
Tactic intent
Exploiting metadata against privacy
Intent measure
How much private information leaks
Countermeasure
To detect unauthorized accesses and raise alarms.
Source
*The Dark Side of Cloud and Edge Computing* by Klervie Toczé, Maël Madon, Muriel Garcia and Patricia Lago (DOI: https://doi.org/10.21428/bf6fb269.9422c084)Graphical representation